
15 July 2019
Stay on top of data breaches with device compliance rules.
Should the worst happen and a data breach occurs, your company has just 72 hours to notify the appropriate security authorities. Making this happen requires automated procedures to be in place for not only the detection but also investigation and reporting processes.
 By using unified endpoint management (UEM) and its compliance policies, you will not only automate the process of detecting breaches on mobiles devices but also remove the possibility of errors made through human judgement.
By using unified endpoint management (UEM) and its compliance policies, you will not only automate the process of detecting breaches on mobiles devices but also remove the possibility of errors made through human judgement.
When time is of the essence, this is very important. A UEM will also continuously run real-time compliance checks based on criteria such as:
You can also configure your UEM to automate actions to rectify the situation should non-compliance be detected. The steps must escalate from informative to restrictive as follows:
The power of MTD and UEM combined.
Depending on the level of sensitivity and desirability of the data that your business handles, you may need more protection than just a UEM to stay compliant. By implementing a mobile threat defence (MTD) system alongside your existing UEM, you can successfully add another level of security to employee devices to stop attacks that may otherwise breach your system.
MTD tools are highly efficient at stopping breaches through malware, phishing scams and network attacks, and when combined with your UEM, the two form a powerful team. The MTD will serve as threat detection and thoroughly check all apps a user may try and use, while the UEM will serve as the solution to a problem should it occur.
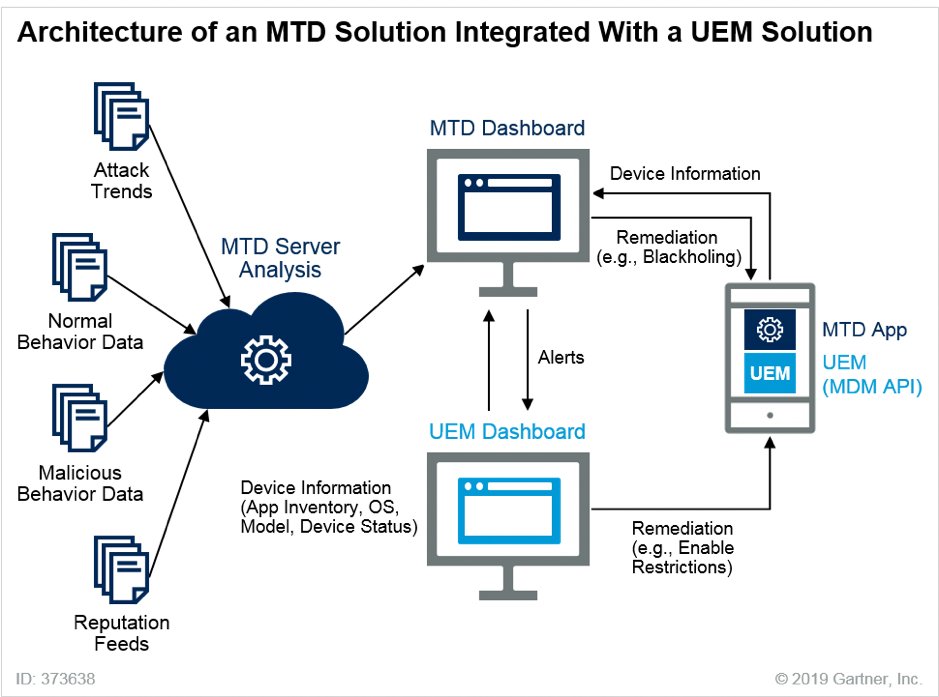
Several major UEM providers have partnered with MTD providers, so it is now easier than ever to seamlessly integrate the two. Although it isn’t always necessary to have both, the cost may well be warranted when compared to a GDPR fine.
Separate work and personal data with UEM tools.
It is essential to utilise your UEM to enforce device-level or container-level passcodes, device encryption, and data security policies, as these will help reduce the impact of lost or stolen devices. Failure to do so can seriously increase a company’s liability should a personal data breach occur. You can use various security controls across multiple platforms, but the right UEM tools provide a single administration console for consistent workflows across most.
Managed apps in iOS.
When working with iOS, Apple provides the ability to separate work and personal data with managed apps using an MDM profile through UEM tools. This process allows for a user to install and maintain their apps, while IT will regulate the business approved apps. Users are not able to transfer data between the two sets of apps to prevent data leakage, however, users can copy and paste text though, which does leave a gap in the system.
Work profile in Android.
Android management allows for users to have their own profile loaded with whatever apps they please, as well as a work profile that will serve as an OS-level container. Both profiles can have the same apps, but only the work profile will be seen and managed by the UEM and IT.
Android work profile has many features that are critical for GDPR compliance.
Insert Table 2 from the Gartner document.
Windows Information Protection (WIP).
This built-in system keeps personal and business data separate by classifying data based on its origin. It can determine if the data comes from a business approved app or a personal one and will stop interactions between the two. For example, it won’t allow users to copy and paste from a business email to a social media app.
By enforcing a WIP policy and using a UEM, you can:
To find out more about how the GDPR could affect you and your business, or if you’re worried about any data leaks, you should speak to a GDPR expert. Every business is different, but the end goal of GDPR is the same for everyone - protecting the private data of all European citizens, no matter where they work or live.
Related Blogs
3 Strategies to Reduce Telecom Cost