
22 March 2018

Yet, according to Gartner, most companies are only using 10% of EMM's functionality, usually just Mobile Device Management and Mobile Application Management. Advanced features, such as Mobile Identity, Mobile Content Management and containment, are used by a far smaller percentage, with few clients using all five components of EMM.
"On average only 10% of total EMM functionality is being used across organisations, although what functionality is used varies greatly by type of organisation. The most advanced EMM deployments are typically using between 30% to 40% of total EMM functionality, but this is unusual for most organisations."

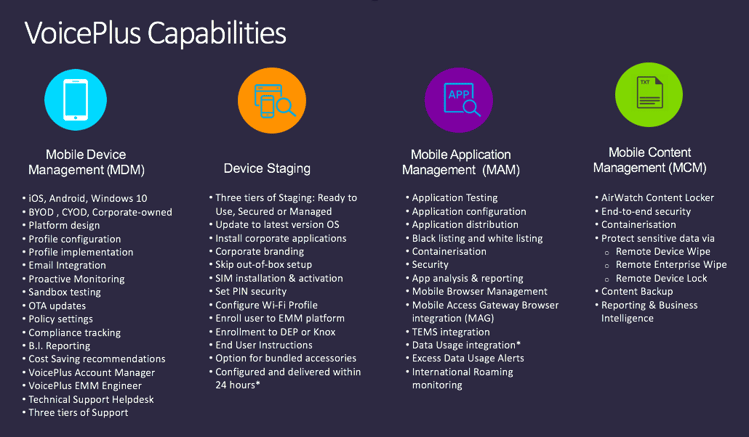
MDM is the key enabler to the glue of EMM. MDM has changed from being a stand-alone product category doing basic policy management, such as passcode enforcement and device wipe, to a required feature within EMM suites. MDM controls have evolved across all operating systems and have expanded into traditional desktop management with Windows 10 and macOS. In addition, Gartner has seen the expansion of management to include advanced IoT devices and Linux. Each OS offers similar basic controls, but advanced controls — such as OS version control for Windows 10 devices, automatic device staging for iOS with Device Enrolment Program (DEP), and the ability to apply different policies to work and personal environments with Android for Work and Samsung's Knox — vary greatly.
Gartner considers MDM a key requirement for enterprise-owned devices. However, we are seeing increased user push-back regarding MDM around privacy and legal concerns, which are often based on a user's misunderstandings of MDM's capabilities.
MAM facilitates the deployment and operational life cycle management of mobile apps. This includes administrative push, user-initiated deployment and updating of custom and public (app store) apps, and management of associated app licenses. User-initiated deployment is facilitated via an enterprise app store, which typically is presented as a web-based portal or a mobile app. License management should support the major enterprise or volume-licensing mechanisms, such as Apple's VPP. MAM also includes the ability to identify or tag apps as "managed" enterprise apps (versus personal apps in BYOD and corporate-owned, privately enabled [COPE] use cases), apply management and security policies to these apps, and selectively wipe them and any associated data from the device.
Although the term is used in several ways in the industry, "containment" here is shorthand for an extended set of capabilities that facilitate separation of business and personal data, including PIM clients, preconfigured public or independent software vendor (ISV)-provided mobile apps, and application extensions, such as SDKs or app wrappers:
Many users no longer have only one device. They frequently have a smartphone, a tablet and a laptop; and, they may want to use these devices as part of a BYOD program. As a result, organisations must be able to determine not only who is connected to the network, but also whether they are connected with a corporate-authorised device. This is why Gartner recognises MI as a key capability of EMM. MI typically is done using digital certificates, but also can be accomplished with other technologies, including biometric and token-based authentication.
Gartner has seen the initial convergence of EMM with IAM tools. This has resulted in several EMM vendors enabling IAM functionality, such as SSO and acting as identity providers. Gartner also has seen the converse, with several IDaaS vendors now offering basic EMM functionality.
The next wave of mobile identity will be context-based, with authentication identifying not only the user and device, but also where and how a user connects to the network (that is, in the office, at home, on a public Wi-Fi or out of the country). Based on these contextual values, MI will grant the user different levels of access. Gartner also expects to see artificial intelligence (AI) used to make critical access decisions. Over the next two years, Gartner expects context-based mobile identity to become standard functionality within EMM products.

Protecting enterprise data on mobile devices traditionally has been based on a multi-pronged approach of encryption of data at rest, in use and in motion, as well as device- and app-level policies, such as screen lock timeouts, PIN enforcement and open-in restrictions. However, these oblique protection approaches are rendered useless once data leaves managed devices and networks. Users can and often do get around such controls by emailing enterprise data to outside parties or personal email accounts, or by copying data to their PCs, where open-in restrictions are absent. In response, there is a growing need to protect data intrinsically and/or implement a rights-management-based approach to mobile data protection.
File-level encryption products encrypt the individual files themselves (rather than simply encrypting stored data and network tunnels) and facilitate managed file access through PKI, such that data can be protected wherever it is stored or accessed. No one without the encryption keys can access files protected in this manner.
Rights management products extend IAM frameworks to provide control over file operations for frequently used file types, in addition to file access. These products enable an organisation to restrict who has permission to read, edit or delete a file, or forward a file via email. Such products typically also facilitate file-level encryption as part of their mobile data protection schemes. Effective data classification, therefore, is critical to making a rights management approach work.
Some EMM vendors are building file-level protection and/or rights management capabilities as adjuncts to their core products; whereas others are enabling file-level protection by synergistically and tightly integrating their EMM systems with general-purpose IAM products. As with device-, app- or content-level policies, EMM should provide a single point of administration for encryption and access/rights policies where these capabilities are present.
Although 2017 was the fourth year of the EMM Magic Quadrant, Gartner reports that it continues to get enquiries about MDM from users who are unaware of the term EMM.
EMM is designed to take clients' needs past basic MDM, however, EMM is quickly no longer meeting the requirements for organisations as client computing merges with mobile computing to form end-user computing groups. This has created the need for a single solution to manage both traditional client devices as well as mobile devices.
Also evolving in this space is the need for some IoT devices to also be managed under the same end-user computing group.
Gartner defines unified endpoint management as a single solution to manage traditional, mobile and EMM-manageable IoT devices.
"We expect this definition to evolve over the next several years as devices continue to change and drive new management requirements. However, it is clear that the diversity and number of devices will continue to grow, and IT organisations must be ready."
Source: Gartner Magic Quadrant for Enterprise Mobility Management 6.8.17
Analyst(s): Rob Smith | Bryan Taylor | Manjunath Bhat | Chris Silva | Terrence Cosgrove

3 Strategies to Reduce Telecom Cost